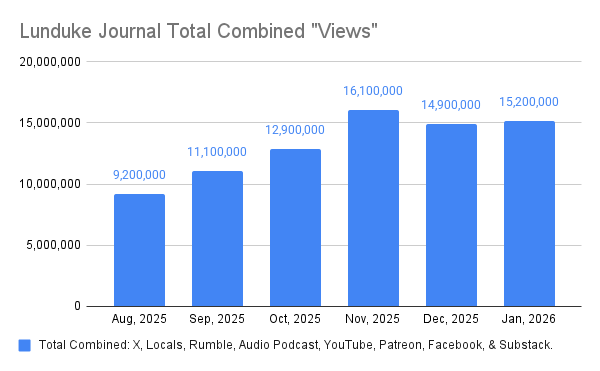
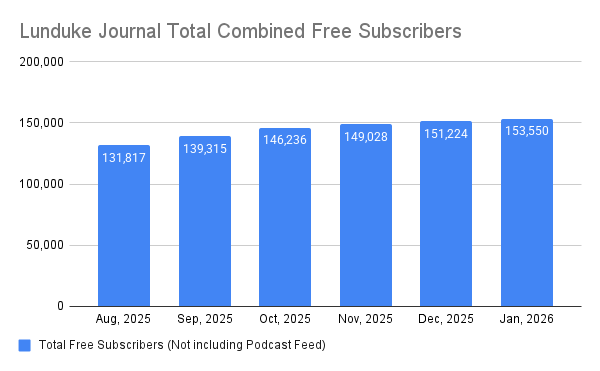
Let’s face it, being prepared for a complete and total loss of Internet access is a good idea. Whether it be for a day, a week, or permanently -- the odds of facing a total Internet outage is close to 100%.
Being prepared for such an eventuality is not a terrible idea.
Get caught up on parts 1 & 2 of the “Digital Prepping” series:
In this installment, we’re going to talk about storage.
Both the storage of your data… and how to physically store your electronics in order to safeguard them in the case of any number of disasters — including EMPs (Electromagnetic Pulses) and Floods.
Planning your backup hardware and file systems
Let’s start with planning for effective backups of your data — because, remember, there is no Internet access. Which means that no matter how well backed up “to the cloud” your data is… you’ll have no way to get to it.
In fact, if the Internet is offline for good? That data is just plain gone.
Finished. Kaput. Finito. Doneskies.
You need to have local copies of all of your data — at least all of the data that you care about. And you need to decide what storage hardware you will use based on a number of factors:
How reliable and resilient is that storage?
How large (in terms of both data it can store, and in physical size) is that storage?
What are your options for accessing that storage (read: mounting that drive) from other computers or devices?
Do you have the necessary types of connectors (USB-C, USB-A, Micro USB, SCSI, CF, SD, etc.)?
What Operating Systems, on your various devices, can read the file systems on that storage?
These may seem like trivial questions right now… but imagine the following:
You no longer have access to the Internet and
You may also not have access to a computer/tech store to buy more equipment or adapters.
Which specific types of connectors your storage drives have — and which file systems they use — is absolutely critical. The most critical part being that you have reliable ways to use them.
Now. Let’s talk about a few of the available storage options.
First… traditional hard disk drives. Those can be absolutely massive in terms of total storage size (and excellent in terms of speed). And, when talking about massive amounts of storage (10 TB +), it’s hard to beat these in terms of price (with 15+ TB models often being available for less than $300).

But, while these are fairly small… they’re not super small. And, because these are spinning, traditional hard disks… they are prone to damage from drops, shakes, and the like.
So, let’s also think about flash storage for a moment. Specifically… USB Flash drives.
The benefit here is that they are both quite small, a bit more forgiving of shaking/dropping, and you can buy them incrementally. Bit by bit. A 128 GB drive here. A 256 GB drive there. Slowly, cheaply, adding to your overall data backup strategy.

There are even a few models of USB flash drives that contain multiple, switchable connection types (such as both a USB-C and USB-A). This is incredibly handy when you want maximum compatibility with a wide range of computers, phones, and tablets.
One big downside to USB flash drives is that — if you get to several TB of storage — the total price is going to start getting significantly higher than traditional hard disk drives.
But, if you don’t plan to have more than 1 or 2 TB of backups, this may not be an issue.
Which brings me to ultra-small, removable flash storage, primarily: SD and Micro SD cards.

If you have your data backups on a series of Micro SD cards (which you can get in 1 TB models nowadays), the total physical footprint of your backups is going to be incredibly small. No more than a couple inches, at most, if you have a large number of them.
But the price is going to be far higher (per TB) than hard disks.
Whatever specific backup hardware you elect to use… do trial runs of accessing that data. Use the exact hardware you plan to have with you in the case of total loss of Internet — and verify that you can access your backups.
I can’t stress enough the critical need to do trial runs of accessing your backups. Regularly.
How to store long-term data backups
Let’s say, hypothetically, that you have decided to use a combination of USB Flash Drives and SD Cards for data backups.
Ok. That works. Small, light, and you can add to them incrementally.
But how, exactly, are you going to physically store your… storage? How are you going to protect your data in the case of disaster?
Electromagnetic Pulse
An EMP (or Electromagnetic Pulse) can wreak havoc on your storage devices — and by “wreak havoc”, I mean “totally destroy and make your data go bye-bye.”
There are a number of different kinds of EMPs — ranging from naturally occurring (such as lightning) to the weaponized (such as a nuclear blast).
While we can hope that nothing like that ever occurs or impacts your electronics and data… it doesn’t hurt to be prepared.
So. How, exactly does one actually prepare for something as catastrophic to electronics as an EMP?
Simple: With a Faraday Cage.

A Faraday Cage, in simplest terms, is an enclosure that blocks electromagnetic radiation and fields. Even getting blasted the 4.6 million volts of a massive Tesla Coil is perfectly safe inside of a well-built Faraday Cage.
How do you get a Faraday Cage, you ask?
Turns out, if you don’t want to build your own, there are many for sale (cheaply). Ranging from “Faraday Boxes” (which can fit a number of small devices) to “Faraday Bags” designed to hold a smartphone.
With an average price being sub-$50 for good quality ones.
Not only do these help block wireless signals — in case you are worried about privacy — but they can also provide significant protection against EMPs.
Note: Many people believe that placing electronics within a Microwave Oven will protect them against an EMP. This, as a general rule, is simply not the case. While a Microwave Oven usually provides good insulation against many types of radiation (including many types of wireless signals), very few Microwave Ovens are any match for an EMP. You want a true Faraday Cage.
Flood & Fire
Let’s say you have a Faraday Box and you are using it to store your storage drives with all of your data backed up on them.
What about other types of disasters? What happens in a flood? Luckily, there is a great way to protect your backup storage during a flood: A dry bag.

These Dry Bags tend to mostly be used by those doing a lot of boating, kayaking, and the like. They seal up nice and tight and keep the things inside them wonderfully dry.
Cheap ($20 for a good Dry Bag), and they come with the added bonus that they’re built to be grabbed and easily carried. Works just as well for a number of backup drives as for a smartphone. Handy, right?
So. What about a fire?
Well, that one is a little trickier. It’s difficult to safeguard electronics from the brutal heat of a fire. But what you can do is make sure your backup drives are carefully stored in something that’s easy to grab and take with you in a hurry.
Like a Dry Bag.
Recommendation: What if you backed up all of your data to a series of Micro SD cards, placed those into a Faraday Bag, and placed that Faraday Bag inside of a Dry bag?
Easy to grab, small, light, and protected from both EMPs and flooding. All on the cheap. Not bad, right?
Don’t forget your other electronics
All of that is great… but there is one critical thing to remember in all of this:
Every piece of electronics you own is susceptible to the same sorts of dangers as your data backups. If an EMP goes off, your smartphone and computer are toast. In a flood, your tablet isn’t going to fare well.
What can you do? Well. Here’s one idea:
Do you have an old smartphone or tablet? Something that, perhaps, isn’t the latest and greatest… but would still be handy if you had nothing else?
Put that old, unused smartphone or tablet into that Faraday Bag or Box. First make sure the battery is ok and not leaking — then store it (with charging cables and needed adapters) near your storage.
Now, no matter what happens, you have a backup system. Ready to go. Even in a horrible disaster. No Internet required.
Recommendation: Want to feel extra secure? Have a backup of your backup. Two boxes or bags with your data backups. Stored in two different locations. Just in case.
Your Homework for Part 3
Ready to put this into action? It’s easy to get started in a meaningful way, by doing the following two (completely free) steps:
Figure out how much total data storage you need for your backups.
Decide on your preferred way to store all of that.
Once you’ve done that, the next steps are up to you. But now you know what you might need. And knowing, as G.I. Joe says, is half the battle.
See you in Part 4 of Digital Prepping. We’ve got a long journey ahead of us.