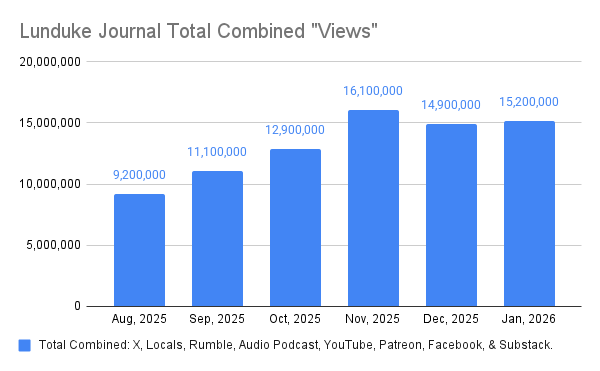
:(){ :|:& };:
That simple line has been crashing systems in the Linux world for years — It is known as the (infamous) “BASH Fork Bomb”.
When run in a GNU/BASH shell, this BASH variant of the Fork Bomb will bring your average Linux system to its knees, lickety-split. A mere handful of characters that can cause a computer to cry “Uncle.”
But what, exactly, is a “Fork Bomb”? How do they work? And where on this green Earth of ours were they first created?
Come with me on a journey into the history, design, and usage of one of the most dastardly ideas in all of computing… of The Fork Bomb!
What is a Fork Bomb?
The idea of a Fork Bomb is simple: Create a piece of code that does one thing and one thing only: replicate running instances of itself. And do so as quickly as possible.
Here, a visual will help drive the idea home.
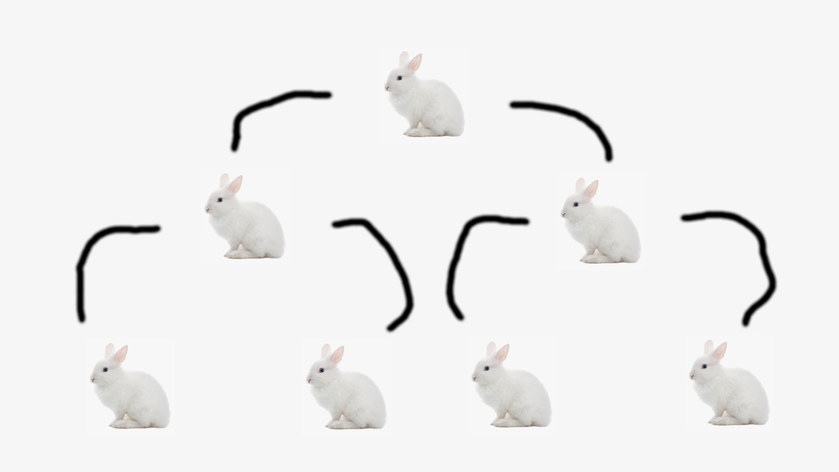
In this case each Bunny Rabbit represents one instance of the Fork Bomb. Each bunny makes two new bunnies. Quickly. Multiplying like, well, rabbits.
Each of those adorable little bunny rabbits may not take up much RAM… or much CPU time… but imagine 20 of them. Or 1000. Or, like, a bazillion?! That Fork Bomb will continue making running copies of itself just as long as the system allows it to (by continuing to have available memory or not fully crash).
With how quickly each Fork Bomb replicates itself… and the number of copies growing exponentially… you can see how they can become a problem in a hurry. Often causing a system to lock up quicker than you can say, “Maybe I shouldn't have pressed Enter.”
A real-world example… and how it works
Let’s take a look at that BASH version of the Fork Bomb again (as that is one of the most popular and famous examples).
(If you don’t know how BASH scripting works, no worries. I’ll break it down… make it nice and easy.)
:(){ :|:& };:
Ok. So how does this, ridiculous looking, collection of semi-random seeming characters, actually work?
Let’s break that apart into multiple lines to make it all easier to read.
: ( ) {
: | : &
} ; :
This… is a BASH script function.
But there’s something… weird about it. Note the many usages of “:”? In this case “:” is being used as a function name.
“Why is using “:” as a function name weird,” you ask?
Because, on most UNIX-y systems, it is not allowed to use a character in a function name other than letters and numbers (and underscores). But the GNU version of BASH — which is commonly used on oh-so-many Linux systems — allows : and so many other characters to be used.
Why does GNU allow a “:”? Who knows. GNU be crazy.
Regardless…
Let’s replace the “:” in that BASH script with “rabbit”. That will, in addition to making it run on more UNIX systems, make this a bit easier to read.
rabbit() {
rabbit | rabbit &
}; rabbit
There. So much better. Here we go. Line by line.
Line 1: rabbit() {
That first line does something simple. It defines a function named “rabbit”. That’s it and that’s all.
Line 2: rabbit | rabbit &
Line 2 is the insidious part.
It calls the function named “rabbit”, and sends the output of that function to the function named “rabbit.”
But, here’s the thing, there really isn’t any output of the “rabbit” function. So this is really just a fancy way of calling the “rabbit” function twice… at the same time.
Yeah. The “rabbit” function calls itself, from within itself, then calls itself again.
Oh, and that “&” at the end? That's the BASH way of telling “rabbit” to run in the background.
The net result? Every “rabbit”, makes two new “rabbit”s.
Line 3: }; rabbit
That last nine simply ends the “rabbit” function… and then calls itself.
Note: I highly recommend not running this code on your system unless you do so in a virtual machine. Without taking the proper precautions… this will bring your system to its knees.
Every variation of a Fork Bomb operates in a roughly similar fashion. A small piece of code that creates copies of itself… repeatedly. Thus eternally replicating itself until the system runs out of resources.
The first Fork Bomb
The very first known usage of a “Fork Bomb” was way back in 1969 at the University of Washington.
There, a Burroughs B5500 computer had been installed three years earlier. A big computer that provided the first time-sharing system on the University of Washington campus (through a series of dial-up modems running at 110 baud). This was also the first computer at the University of Washington to provide disk storage for user files. Pretty cool.

On that big, beautiful Burroughs B-5500, someone reportedly wrote a small bit of code that would make two copies of itself — over and over again — until the memory of the machine was full and the entire system would crash.
That intrepid programmer named that tiny little program, appropriately: “RABBITS”
Fun historical tidbit: RABBITS for the Burroughs B-5500 was not, technically the first computer virus. That distinction appears to go to the 1971 “Creeper Virus”. While RABBITS predated Creeper by a good two years… RABBITS doesn’t really act like a virus. It requires a user to explicitly run it in order to cause its own mischeif.
The 1974 “Wabbit”
A similar piece of code was written on an IBM System/360, a few years later, in 1974. Clearly inspired by “RABBITS”, this new code was called “Wabbit” and was, as Elmer Fudd might say, quite “wascally”.

Legend has it that the individual who created “Wabbit” ran the program on the System/360 at work… causing the entire system to crash. The man, again according to legend, lost his job.
Fun bit-o-trivia: As years went on any program that would self-replicate when ran by the user… but wasn’t actually a virus… would become known as a "wabbit.” in honor of this particular event.
Some other variations on the Fork Bomb
There have been Fork Bomb type bits of code written in just about every language you can imagine. At the beginning we covered how to write a Fork Bomb in BASH. But, because this sort of mayhem is simply too much fun, below you will find code to create similar bits of functionality in several other programming languages.
Enjoy.
Just… you know… try not to get yourself fired.
Fork Bomb in C:
int main(void) {for (;;) {fork();}}
Fork Bomb in Python:
#!/usr/bin/env python
import os
while True: os.fork()
Fork Bomb in Ruby:
#!/usr/bin/env rubyloop { fork { bomb } }